
Detection and blocking of toxic flows
Real-time alerts and risk anticipation + identification
Automatic cyber security reports on the status of the information system
Monitoring and threat understanding made easy with Serenicity Control
Suitable for all types of networks
A simple solution accessible to all
The Detoxio solution analyzes and blocks toxic flows that can alter, destroy or steal data from organizations.
In physical or virtual form, Detoxio can be quickly installed in many environments.
Comes with an intuitive and comprehensive interface
View threats on your network in real time with Serenicity Control and remedy weaknesses quickly.
Discover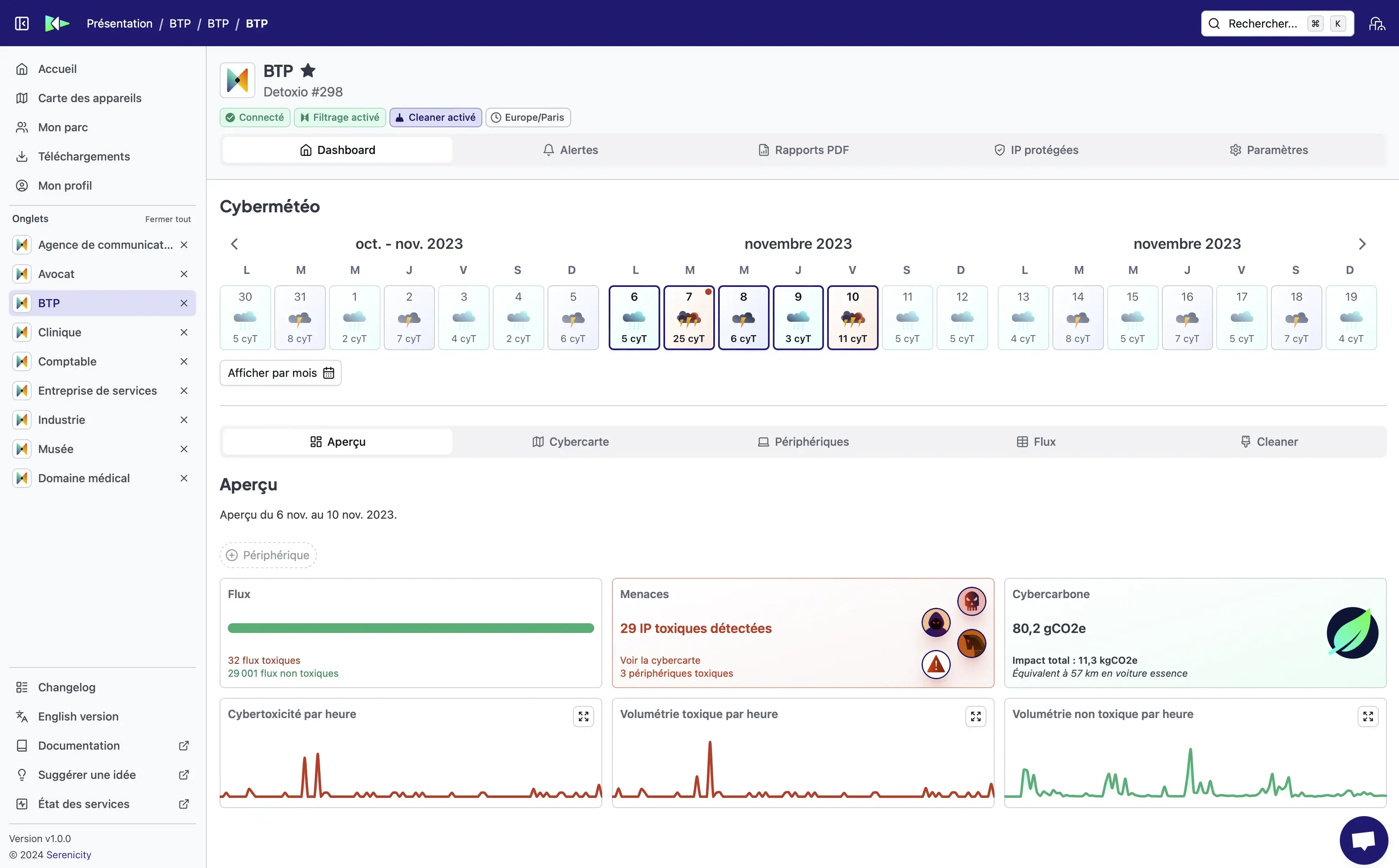
Serenicity Cerbère
The Serenicity Cerbère database is constantly updated with the latest indicators of compromise based on our patented technologies and our agreements with the authorities.
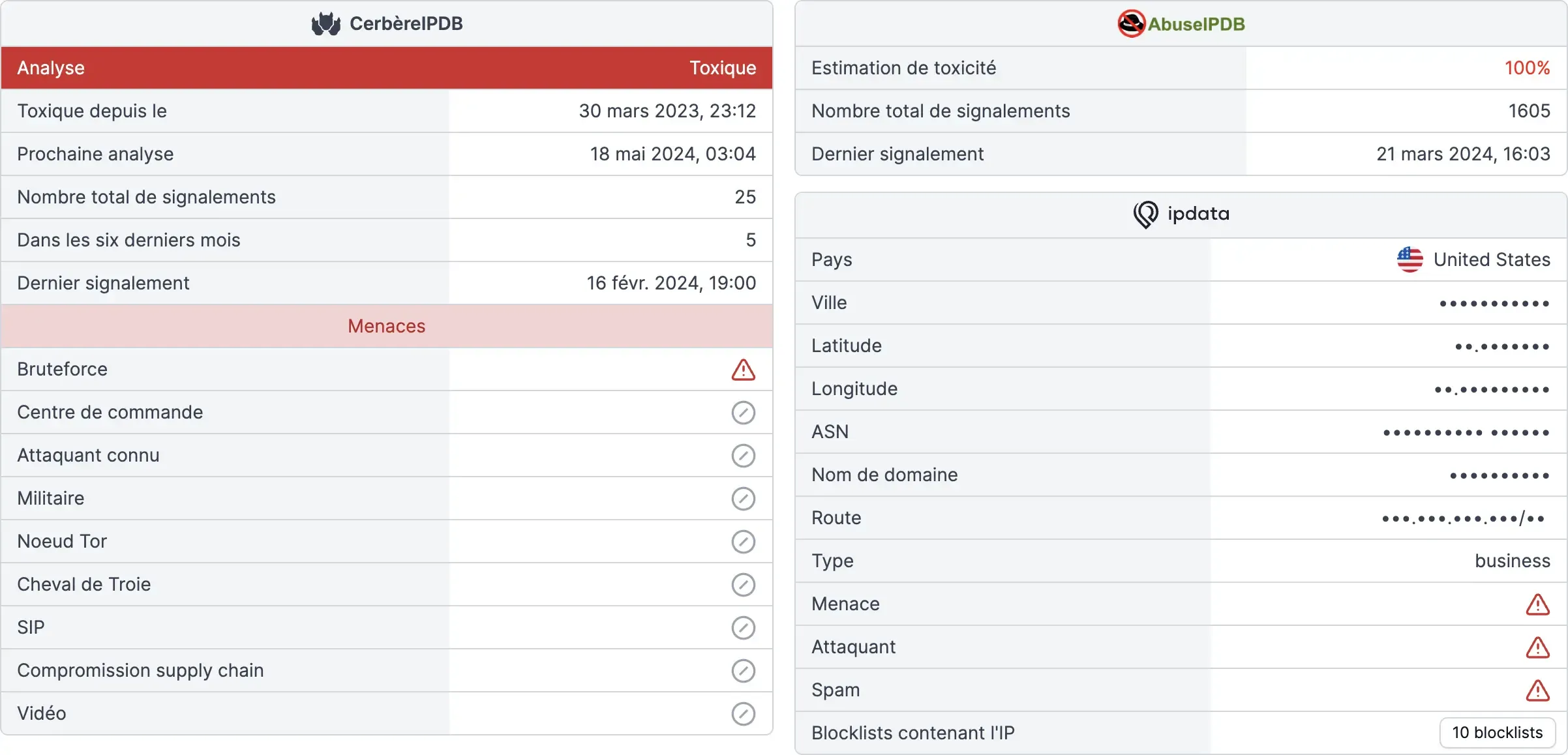
Integrated with solutions
Serenicity Cerbère is continuously updated with Detoxio and Cymealog to quickly detect and block suspicious activity and malicious behaviour before it causes damage.
Connected with our partners
Our agreements with the authorities and our private partners guarantee a constant flow of intelligence on the latest and most advanced threats.
Precise qualification
Serenicity Cerbère provides accurate and reliable information on threats in order to protect your information system: location, typology, host, etc.
Behavioural analysis
Indicators are updated in real time based on Internet threat activity to provide comprehensive and proactive protection.
Instantly block and monitor toxic flows
Advanced security features, configurable alerts and automatic setup allow you to focus on what really matters.
Simple installation
Threat protection from the moment your network is switched off.
Flexible
Deployment possible in dedicated equipment, server or VM.
Autonomous
Automatic updates with new features.
Security
Supervision and filtering of toxic and non-toxic flows in real time.
Alerts
Send customizable alerts when threats are detected.
Threat update
Integration of the Serenicity Cerbère database several times per hour.
Technical specifications
Protect your organization by filtering data flows in and out of your network.
Filtering
Flow processing via a transparent bridge.
Protection
Compatible with all types of information systems.
Network
Custom network interfaces (from 1 to 10Gb).
API
Access to your data via a REST API.
Discover the Detoxio range
Each Detoxio solution is designed to meet specific needs. Need advice? Contact us
Essential

Detoxio Essentiel is equipped with a 1 Gb/s Ethernet network bridge for monitoring flows from a single network segment.

Integral Multi

Detoxio Integral Multi is equipped with 3 1Gb/s Ethernet network bridges enabling supervision of flows from 3 network segments.

Integral Rack

Detoxio Integral Rack is equipped with 4 1Gb/s bridges and 2 SFP+ 10Gb/s bridges, enabling supervision of flows from 4 Gbe segments and 2 fiber segments.

Central

Detoxio adapts to all types of physical or virtual architectures. Originally designed as a transparent bridge, Detoxio can route traffic from a Layer 3 core network. Contact us for a customized study.
Contact us
The Detoxio solution for all organisations
From small businesses to large corporations and government agencies, all organisations face increasingly sophisticated and varied threats.
Data security is crucial to preserve the trust of your clients and the continuity of your business. Detoxio includes measures to prevent, detect and respond to cyber attacks.
Spot and block data leaks
Detoxio detects abnormal flows and blocks data exfiltration attempts caused by malware present in your information system.
Any connected machine is a target
Computers, servers, but also printers or any equipment connected to the network is a potential target for cyber attacks. Detoxio and Control allow to map all toxic and non-toxic network flows.
Prevent ransomware attacks
Backups alone are not enough to guarantee complete security against ransomware. Detoxio blocks traffic to command centres and stops the reloading of ransomware.
Spotting the warning signs
In addition to spotting weak signals by triggering alerts, Detoxio allows you to implement preventive measures to strengthen the security of your network and protect your sensitive data.
Sovereignty by design
Our solutions designed and developed in France are hosted in Europe.
Our products ensure the security of your data, particularly with regard to RGPD requirements and extra-territorial laws.
Are you cyberprotected?
Whatever the size of your organization, Detoxio is a SOCable (Security Operations Center compatible) solution.
Our partners ensure the monitoring and protection of your assets with our solutions.
